Cyber Essentials Plus: Why Our Clients Pass Without Scrambling
Cyber Essentials Plus certification should confirm what's already true, not require a scramble. Here's how we make compliance a natural outcome of proper IT management.
Cyber Essentials Plus certification should confirm what's already true, not require a scramble. Here's how we make compliance a natural outcome of proper IT management.

Most businesses treat Cyber Essentials Plus like an exam they need to cram for. They spend weeks fixing things that should have been right all along, panic about the audit, and breathe a sigh of relief when they scrape through.
Our clients don't do that. They pass because they're already running their IT the way Cyber Essentials Plus expects. The certification is just paperwork confirming what's already true.
Here's why that matters, what Cyber Essentials Plus requires, and how we make compliance a natural outcome rather than a project.
Cyber Essentials Plus is the UK government's baseline cyber security standard with teeth. While the basic Cyber Essentials certification relies on a self-assessment questionnaire, Plus adds an independent technical audit where an assessor tests your systems.
The scheme covers five control areas designed to stop the most common internet threats:
During a Plus audit, the assessor will scan for vulnerabilities, test workstation security, simulate malware and phishing attacks, and sample devices to prove your controls work in practice, not just on paper. Any problems found typically need fixing within 30 days before certification is awarded.
For many government contracts and MOD supply chain work, Cyber Essentials or Plus certification has been mandatory since 2014. Beyond hard requirements, it's increasingly expected by larger clients as proof you've taken verified steps to address commodity attacks like password spraying, malware, and basic exploitation.
The struggle with Cyber Essentials Plus comes from treating it as a one-off certification project rather than how you should be running IT anyway.
Here's what typically happens: a business decides they need the certification, downloads the requirements, realises they're not meeting them, and scrambles to fix everything before the audit. Patch cycles get rushed. Access controls get bolted on. Documentation gets written retrospectively. The whole thing becomes a stressful, expensive exercise that feels disconnected from day-to-day operations.
Our approach is different because we build these controls into how we manage systems from day one:
We assume you'll be audited tomorrow. Every device we deploy is configured to Cyber Essentials Plus standards as default. Clean builds, hardened settings, MFA enforced, no exceptions. When audit time comes, there's nothing to fix.
Patching happens automatically, not as a project. Our patch management runs continuously across Mac and Windows devices. Critical updates deploy within days, not weeks. We don't need a pre-audit scramble because your systems are already current.
Access control is built in, not bolted on. MFA, strong passwords, principle of least privilege – these aren't special measures for certification. They're how we secure your environment all the time.
We scope accurately from the start. Many businesses fail audits because they didn't properly define what's in scope. We maintain clear asset registers, know exactly what's connected to your network, and can produce that documentation instantly.
We monitor and prove it's working. The difference between Cyber Essentials and Plus is evidence that controls are operating. We're already collecting that evidence through our monitoring and management tools, so proving compliance is straightforward.
The result: when our clients go for Cyber Essentials Plus certification, they're not fixing problems. They're documenting what's already in place.
Let me get specific about what each control area requires and how we handle it as standard practice:
The requirement: Properly configured firewalls on boundary devices, unnecessary services disabled, default credentials changed, and clear policies about what traffic is allowed.
How we do it: Every device we manage has its software firewall correctly configured and monitored. We document network boundaries, review firewall rules regularly, and track any exceptions. This isn't audit prep. It's basic network security.
The requirement: Devices and software configured to reduce vulnerabilities, with unnecessary features disabled, default credentials changed, and secure baseline builds maintained.
How we do it: We maintain gold builds for both Mac and Windows devices that meet secure configuration standards. Every new device is deployed from these baselines. Cloud services get hardened according to vendor security frameworks. When you receive a laptop from us, it's already audit-ready.
The requirement: Multi-factor authentication on all remote access and administrative accounts, strong password policies enforced, accounts removed when people leave, and proper privilege management.
How we do it: MFA is non-negotiable across our managed environments. We integrate with your identity provider (whether that's Microsoft 365, Google Workspace, or Jamf for Apple devices) to enforce authentication policies. Access reviews happen quarterly. Departing staff accounts get disabled immediately, then removed after the appropriate retention period.
The requirement: Anti-malware software on all devices, kept up to date, and configured to scan files and removable media.
How we do it: Every managed device runs monitored, managed malware protection. For Macs, we use a combination of macOS's built-in XProtect plus enterprise-grade solutions. Windows devices get Microsoft Defender or equivalent, managed centrally. We track protection status across the fleet and alert on any gaps.
The requirement: Patches deployed promptly (within 14 days for critical updates), with a process to track and install updates across all devices and software.
How we do it: This is where most DIY attempts fail. We run automated patch management that tracks updates across operating systems, browsers, business applications, and third-party software. Critical patches deploy within our change control windows (typically 3-7 days for most clients, faster for emergencies). You don't think about it. It just happens.
If you're considering Cyber Essentials Plus, you probably want to know where you stand before paying for an audit.
We've built a quick readiness assessment that gives you a realistic sense of your current position. It's not an official tool and won't guarantee you'll pass, but it highlights the major areas auditors will examine and where you might have gaps.
Think of it as a milestone check rather than a practice exam. It takes about 10 minutes and gives you specific areas to address before you commit to the full audit process.
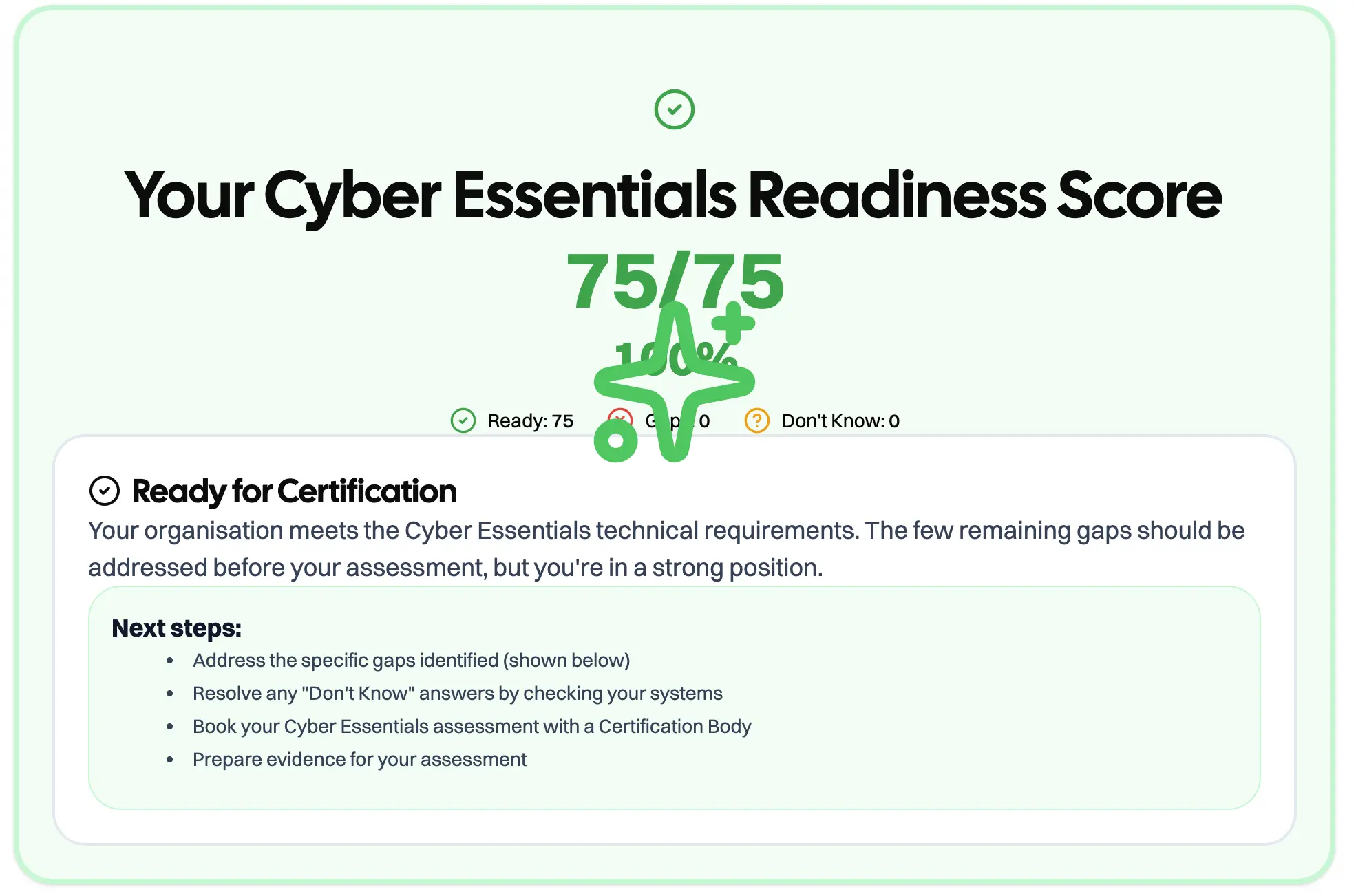
Here's what matters more than the certification itself: if you're running your IT to Cyber Essentials Plus standards, you're addressing the attacks that happen to UK businesses.
The controls aren't theoretical. They're based on NCSC analysis of real incidents. Properly implemented, they stop commodity malware, credential theft, basic vulnerability exploitation, and phishing campaigns – the attacks responsible for most SME breaches.
The certification proves to clients, partners, and government procurement that you've had these controls independently verified. But the real value is knowing your IT security is solid because you're doing it right all the time, not just during audit season.
If you're pursuing Cyber Essentials Plus certification, we can help in three ways:
If you're already a Stabilise client: We'll review your environment against the requirements, document what's already in place, identify any gaps, and help you through the certification process. In most cases, you're already 90% there.
If you're not our client yet: We can perform a readiness assessment, implement the required controls, and manage your systems to maintain compliance long-term. The certification becomes a natural byproduct of proper IT management.
If you just need the certification: We'll scope your environment, implement the technical controls, help you complete the self-assessment, and prepare you for the Plus audit. But honestly, if you're doing this as a one-off project, you're missing the point. These controls should be permanent, not temporary.
The businesses that struggle with Cyber Essentials Plus are the ones treating it as a separate concern from their normal IT operations. The ones that pass easily are running their IT properly in the first place.
We build that proper IT management as standard. When certification time comes, you're not clameringto fix things. You're documenting what you already do.
That's how it should work.
If you want to check your current readiness, try our assessment tool. If you want to talk about making compliance effortless rather than stressful, get in touch.